Hack-Nos (OS-HAX)
Hack-Nos is another boot-to-root vulhub machine Hack-Nos .This box i believe is an intermediate box.The flag was important then gaining root and i got flag from two ways that was fun.
Breaching Process
Finding IP
- Nmap
Enumeration
- Browsing HTTP service
- Enumerating directory
- Got drupal (further enumerating version from change.log)
Exploitation
- using metasploit
- got reverse shell
Privilege Escalation
- Gaining wget root access to change the passwd file
Let;s Breach :
First IP discovery was important where i use nmap to scan the network
Use the root permission to scan for nmap the network.
The ip was 192.168.1.16.Then i go for surfing and use dirb at background
so the page look like default apache
There was not any juicy thing so i see the dirb scan and found there was a drupal
I cannot login in as james i tried different combination of text got failed.
And then go for the version enumeration of drupal.That was preety easy googeling give me the answer.The version can be seen using
192.168.1.16/drupal/CHANGELOG.txt
wow there was preety good vulnerability
I think about metasploit then fire up the msfconsole and after checking all the drupal eploit one by one i found this was interesting that is giving me persistance shell
chaning the path,ip and port.
wow i got the shell of www-data
Now let's hunt for the high privilege (root).I want to use shortcut key (CTRL + L) to clear screen so i import the XTERM haha (Just for fun).Now it's look like i complete the half task
after importing the xterm then i list the file there was user.txt file
without time consuming i go for the root permission check (which program can run as a root without password).Ka-Boooom the wget command can be run as root
There was an idea of importing any file using wget just using nc and you can catch the req from wget.so,
from victim machine i fire-up the wget (use root.txt file ) and listen in my machine
so the scenario look like this
Victim machine
My machine
Boom the task was completed.
But there was no fun of just going for flag so,i go for the root access to that machine
by changing the passwd file i can get root access
Let's begin the second method
Access the machine using msfconsole as same as above step
Read the passwd file and copy paste into your machine
cat /etc/passwd
(don't see the test file i have done it using test user previously)
pasting into my machine and save as passwd file
then i generate a password(password) and user (codie) in my machine
openssl passwd -1 -salt codie password
then i fire-up the python server in port 80 (make sure the passwd file is in that directory)
python -m SimpleHTTPServer 80
And then import the passwd file into victim machine using wget which will ultimately changing the passwd file which was astounding.
i check the passwd file whether the file was imported or not in victim machine
so, i got this a edited version of passwd file and there was my username as root
Now i use su - codie command to get access to codie account and got succesfull to run as a root
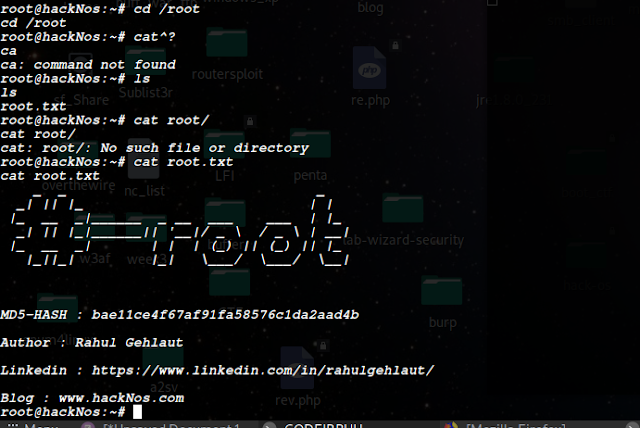
and now the cat /root/root.txt
Boom i got root access





















Comments
Post a Comment