Chanakya Vulnhub Walkthrough
It was the box where you have to have knowledge about using Nmap , dirb or nitko or gobuster ,ftp, ssh and metasploit .In this box we analyze the ftp connection using wireshark and got credentials and after that we gain access shell using ssh and exploit root permission using metasploit.
Breaching Process
Finding IP
- Nmap
Enumeration
- Nmap Deep scan
- Browsing HTTP service
- Enumerating directory
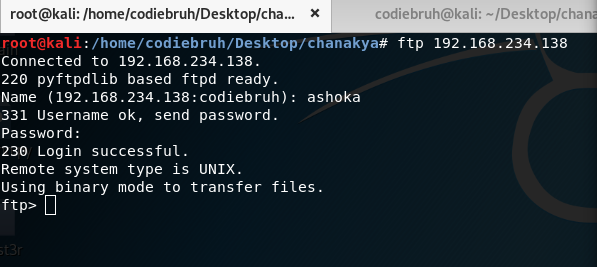
- ftp login
Exploitation
- Generating ssh authorize key
- Gaining access to shell (ashoka)
- Reading chrootkit logs (using metasploit)
Privilege Escalation
- chkrootkit
Let's Breach
Using nmap we scan the network ip in our network
nmap -sn ip_range (use root permission to scan )
After sanning there are only five ip that was not hard for me to find we are using NAT in virtualbox
after finding the ip we go for Enumeration (this is the phase where you have to see every single piece of information)
Browsing the ip we get and we also do a NMAP scan
The page look like this
After the result of nmap we found there are 21,80 port open where i paid attention to ftp mostly
There was no anonymous login and other credentials
and we go for dirb to scan directory
we only scan for .txt file. we found abuse.txt
And the file was encoded in rot13 it was new for me
I copy it and then deoce it from online
Then we found that it was a directory file and it was in pcapng file which can be analyze using wireshark
we found a ftp credentials form ashoka.pcapng
the Username was ashoka
and the password was kautilya
without any delay we login into ftp server
then the ftp connection was in ashoke home directory
After dir then
the list of file we got where .ssh was also there or you can create a ssh folder using mkdir .ssh
after that we generate the ssh key and the password is blank for ssh (we generate in my box)
And then the authorize key
again we login into ftp and upload the authorize key in .ssh folder to gain ssh shell
The upload was succesful
Now,it's time to gain ssh shell
so i ssh in to the victim box
using ashoka user
Boom we got the ssh connection
Now, we exploit the box using python tty shell
using metasploit
paste the shell code of python in ashoka ssh shell and hit enter
As, we hit enter then the metasploit shell will open as sessions
we can check it as
as i got the shell i check for chrookit
see i use the port 4444 for everthing but i didn't get the sudo permission in that port
Then again repeat the method of generating the sehll code of python with port 1234
after trying three times i got exploit using chrootkit
Finally i got the root shell





















Comments
Post a Comment